Platforms rush to deploy autonomous agents for everything from information queries to transaction execution. The enthusiasm makes sense, as agents collapse complexity, translate intent into action, operate while humans sleep, and so on. Yet, there is an increasing gap between agent capability and agent accountability. When your information Agent answers user questions, the stakes are low. But when your Transaction Agent moves capital based on market conditions at 2 AM, the question “who authorized this?” becomes existential.
In 2025, we have been witnessing a quiet revolution: passkeys – cryptographic, phishing-resistant, passwordless credentials are replacing old-school passwords. More than 15 billion online accounts worldwide can use passkeys for sign-in, and adoption nearly doubled in 2024 alone.
For builders of AI-powered systems and specifically the ones designing autonomous agents security for transaction-oriented agents, such as paymasters, this shift presents both an opportunity and a dilemma. Passkeys for AI agents encode human intent: a biometric tap, a fingerprint, or a PIN – something only a real person can provide.
The platforms building for the future aren’t just asking what their agents can do. They want to know: Can we prove which human delegated this authority? And for how long? With what boundaries? The answer increasingly points to a technology that most associate with consumer login flows.
Autonomous Agents Security: Why Traditional Auth Breaks Down?
Conventional authentication assumes that someone is present to type a password or tap their phone. This assumption breaks when your agent needs to execute based on oracle data, respond to liquidation risk, or batch transactions for gas efficiency. Static API keys and bearer tokens, which are the usual approach for machine authentication, persist indefinitely – get hardcoded into config files, and offer zero proof of who created them or why. For instance, when an agent uses a static key to authorize a $500K transaction, you are left to reconstruct intent from logs and hope that nothing was compromised.
Digital verifiable credentials like passkeys rely on human-initiated procedures, as agents cannot directly present these credentials, preserving the chain of trust. This isn’t a limitation. It’s the feature that makes delegation work securely.
Passkey authentication, built on WebAuthn and FIDO2 standards, replaces passwords with cryptographic proof, bound to specific domains. Passkeys are phishing-resistant because the browser enforces that a passkey can only authenticate on the domain where it was registered. No amount of social engineering can trick a user into “entering their passkey” on a fake site, as the passkeys neutralize this threat.
The challenge isn’t giving passkeys for AI agents directly – it’s building the bridge between human authentication and agent authorization. Web3 authentication, also known as decentralized authentication, allows for a secure verification of users on the web. What we need is a framework that preserves the security properties of passkey authentication while enabling agents to operate autonomously within defined boundaries.
If we don’t have a proper delegation layer, we risk undermining agentic AI security, letting long-term misuse, replay attacks, or unauthorized fund movement – all the threats passkeys were incorporated to prevent. Solving this gap is the prerequisite to safely unlocking agentic paymasters and automated on-chain services.
Decentralized Authentication Methods: The OAuth Bridge to Agent Delegation
The solution isn’t giving agents their own passkeys. It’s giving humans the ability to delegate accurate time-limited authority to agents, with cryptographic proof of that delegation. This is where decentralized authentication methods work alongside standard delegation frameworks.
The Authorization Code Grant with PKCE is a common OAuth flow integrating passkey-based user consent into the delegation process. Here’s how it works in practice:
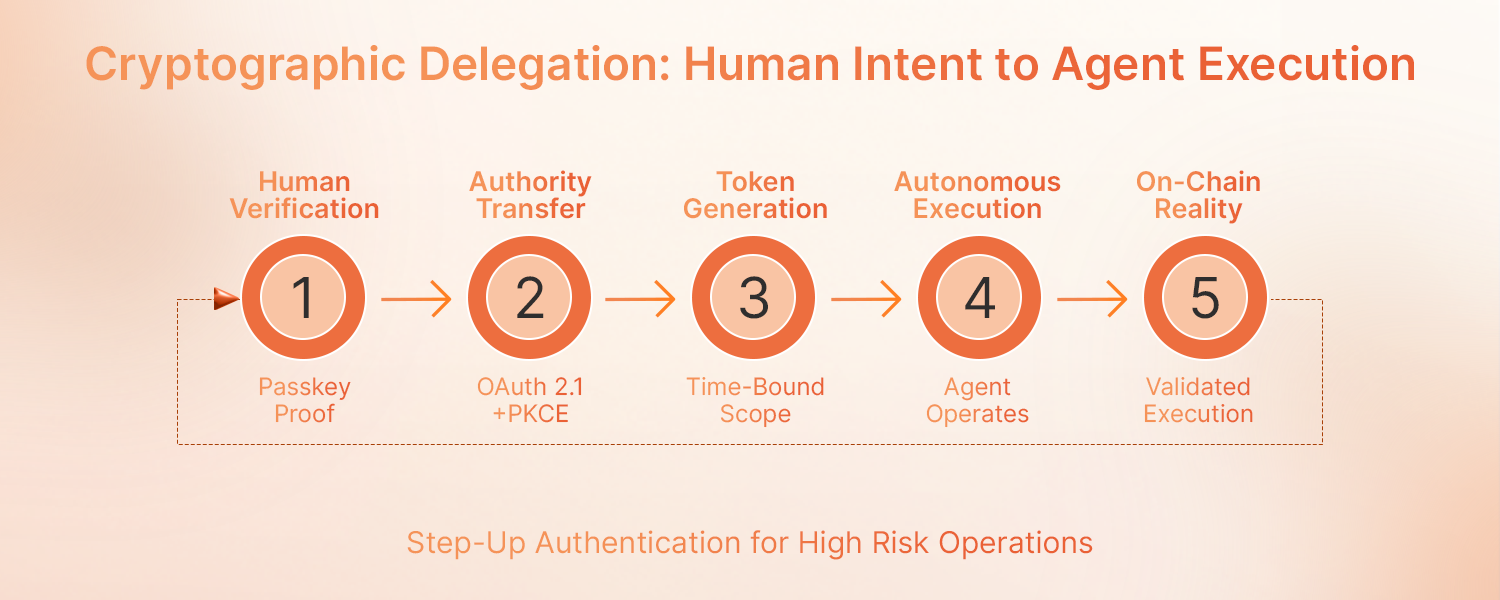
- Step 1: Human authenticates with passkey
A user opens your platform, triggers a WebAuthn ceremony, and verifies who they is who they claim to be – Just cryptographic proof bound to their device and your domain. This implies increased security and privacy for users and the ability for users to have more control over their data.
- Step 2: Human delegates to the Agent
The platform initiates an OAuth 2.1 flow with PKCE (Proof Key for Code Exchange). PKCE prevents authorization code injection by requiring that only the client that began user authentication can exchange the authorization code for an access token. The user sees exactly what they are authorizing: “Allow Transaction Agent to execute swaps up to $10K per hour for the next 8 hours?”
- Step 3: Agent receives scoped token
Instead of sharing credentials, users delegate authority via scoped tokens – allowing agents to execute tasks while keeping user credentials secure. In other words, the agent doesn’t get the passkey, but a temporary access token with explicit boundaries: which operations, for how long, with what value limits.
- Step 4: Agent operates within boundaries
When your agent needs to execute a swap, it presents its token to your smart account infrastructure. The token carries the full delegation chain: which user, which agent, which scope, and when it expires. Every operation traces back to human authorization. Smart contracts permit the use of DAC (Decentralized Access Control) mechanisms to assure that only authorized users interact with a given resource or execute certain functions.
- Step 5: Step-up for sensitive operations
Best practices include enforcing least-privilege access, using transient tokens, and employing step-up authentication via passkeys for sensitive actions. If your agent tries something outside its scope, it prompts the human for a new passkey authentication.
For instance, GitHub already uses this pattern: users authenticate with passkeys, then delegate controlled access to CI/CD agents through OAuth tokens. Smart contract-based authentication makes way for more sophisticated verification processes, particularly useful in scenarios entailing multi-factor authentication or in decentralized autonomous organizations (DAOs). The difference in Web3 is what happens next, and that’s where Abstraxn’s infrastructure connects authentication to execution.
Abstraxn’s Approach: Passkey Authentication as Paymaster Intelligence
The actual transformation happens when passkey authentication stops being just a login mechanism and starts informing the execution infrastructure. At Abstraxn, we have built an architecture where cryptographically-verified human intent flows smoothly to on-chain execution.
The Paymaster Decision Layer
You need intelligence that checks whether this specific operation deserves gas sponsorship. AI Agents decide who pays for gas, in real-time, based on logic, role, and behaviour. Traditional paymasters operate on simple rules: sponsor these addresses, up to this amount. That breaks when autonomous agents make context-aware decisions. Abstraxn’s AI-powered paymaster assesses:
- Authentication provenance: Was this agent authorized via passkey authentication or legacy credentials?
- Token validity: Is the OAuth token still valid?
- Scope compliance: Does this operation fall within delegated permissions?
- Behavioral patterns: Does this align with user history?
- Risk signals: Any anomalies suggesting compromised delegation?
Developers can use Webhooks to implement any sponsorship logic they wish, allowing precise control over which UserOperations should be accepted by the Paymaster. When a Transaction Agent attempts a swap, the paymaster receives full context: the passkey-verified user, the OAuth token with time-bound scope, the agent type, and operation details. It makes a real-time decision: sponsor fully, partially subsidize, or demand user payment.
Execution with Audit Trail
The Bundler executes AI agent-generated operations in batches for speed and cost efficiency. Every transaction carries an immutable audit trail.
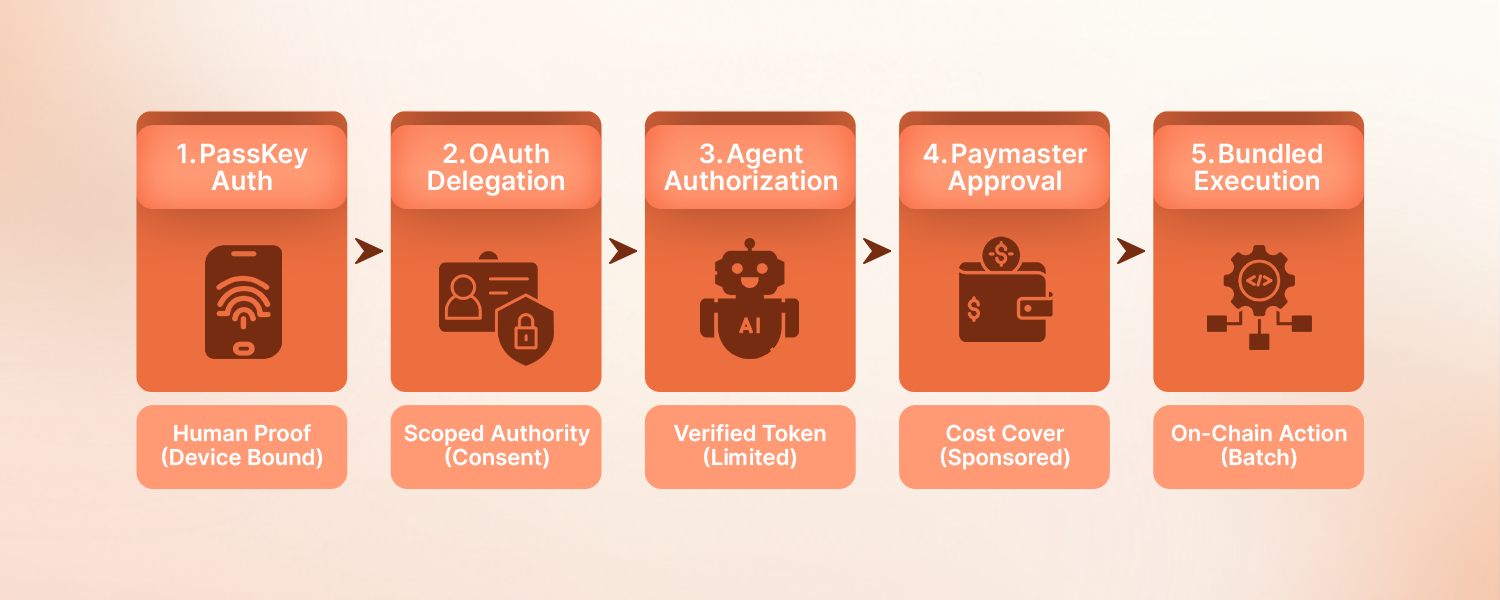
If anything goes wrong, you can track it back to the exact human who authorized it, when, and with what boundaries. It’s not enough to verify identity at login – you need cryptographic proof flowing through every layer of autonomous agents security.
Final Word
Passkeys resolved a decade of identity insecurity. Autonomous agents are solving operational friction. The challenge ahead is combining the two without breaking the guarantees of either. To overcome this, decentralized authentication methods bind off-chain and on-chain trust without central intermediaries. This is the design principle Abstraxn embraces: intelligence that moves at machine speed, with guardrails rooted in human consent and cryptographic certainty.
Passkeys lend us the strongest identity primitive of this era. Executed well – they can give us the safest foundation for passkeys for AI agents, fully autonomous paymasters, and the next leap in trust-minimized automation.




